EQShield safeguards information from loss through backup and recovery. EQShield offers in-line WAF Production for protection requirements.
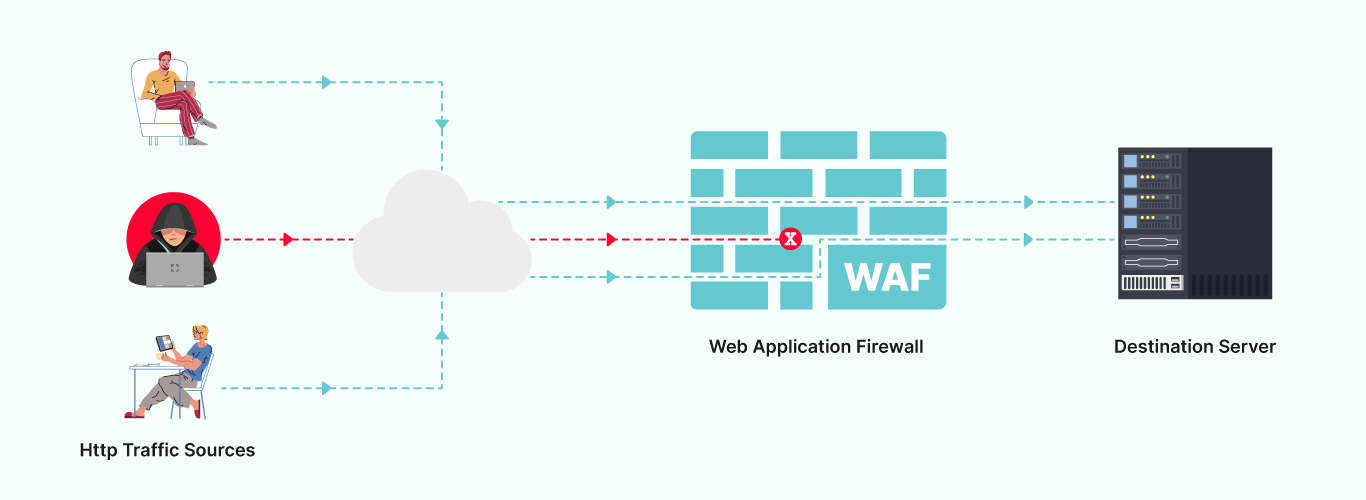
A Web Application Firewall is the first line of defense against sophisticated attacks that would threaten the integrity of your enterprise. The most effective and efficient solutions offer the following WAF capabilities:
WAF security can prevent many attacks, including:
Attackers inject client-side scripts into web pages viewed by other users.
Malicious code is inserted or injected into a web entry field that allows attackers to compromise the application and underlying systems.
Modification of a cookie to gain unauthorized information about the user for purposes such as identity theft.
Attackers tamper with HTTP requests (including the URL, headers, and form fields) to bypass the site’s security mechanisms.
An HTTP flood attack that utilizes valid requests in typical URL data retrievals.
Data scraping used for extracting data from websites.
Aspirapps EQShield provides the following three common protection requirements:
DDoS attack means "Distributed Denial-of-Service (DDoS) attack" and it is a cybercrime in which the attacker floods a server with internet traffic to prevent users from accessing connected online services and sites.
A DDoS attack aims to overwhelm the devices, services, and networks of its intended target with fake internet traffic, rendering them inaccessible to or useless for legitimate users.
Different attacks target different parts of a network, and they are classified according to the network connection layers they target. The three types include:
This type of attack aims to control all available bandwidth between the victim and the larger internet. Domain name system (DNS) amplification is an example of a volume-based attack. In this scenario, the attacker spoofs the target's address, then sends a DNS name lookup request to an open DNS server with the spoofed address.
When the DNS server sends the DNS record response, it is sent instead to the target, resulting in the target receiving an amplification of the attacker’s initially small query.
Protocol attacks consume all available capacity of web servers or other resources, such as firewalls. They expose weaknesses in Layers 3 and 4 of the OSI protocol stack to render the target inaccessible.
An SYN flood is an example of a protocol attack, in which the attacker sends the target an overwhelming number of transmission control protocol (TCP) handshake requests with spoofed source Internet Protocol (IP) addresses. The targeted servers attempt to respond to each connection request, but the final handshake never occurs, overwhelming the target in the process.
These attacks also aim to exhaust or overwhelm the target's resources but are difficult to flag as malicious. Often referred to as a Layer 7 DDoS attack—referring to Layer 7 of the OSI model—an application-layer attack targets the layer where web pages are generated in response to Hypertext Transfer Protocol (HTTP) requests.
A server runs database queries to generate a web page. In this form of attack, the attacker forces the victim's server to handle more than it normally does. An HTTP flood is a type of application-layer attack and is similar to constantly refreshing a web browser on different computers all at once. In this manner, the excessive number of HTTP requests overwhelms the server, resulting in a DDoS.
Log analysis is the process of reviewing computer-generated event logs to proactively identify bugs, security threats, factors affecting system or application performance, or other risks. Log analysis can also be used more broadly to ensure compliance with regulations or review user behavior.
Effective log analysis has use cases across the enterprise. Some of the most useful applications include:
Log analysis tools and log analysis software are invaluable to DevOps teams, as they require comprehensive observability to see and address problems across the infrastructure. Further, because developers are creating code for increasingly-complex environments, they need to understand how code impacts the production environment after deployment.
An advanced log analysis tool will help developers and DevOps organizations easily aggregate data from any source to gain instant visibility into their entire system. This allows the team to identify and address concerns, as well as seek deeper information.
Log analysis increases visibility, which grants cybersecurity, SecOps and compliance teams continuous insights needed for immediate actions and data-driven responses. This in turn helps strengthen the performance across systems, prevent infrastructure breakdowns, protect against attacks and ensure compliance with complex regulations.
Advanced technology also allows the cybersecurity team to automate much of the log file analysis process and set up detailed alerts based on suspicious activity, thresholds or logging rules. This allows the organization to allocate limited resources more effectively and enable human threat hunters to remain hyper-focused on critical activity.
Visibility is also important to IT and ITOps teams as they require a comprehensive view across the enterprise in order to identify and address concerns or vulnerabilities.
For example, one of the most common use cases for log analysis is in troubleshooting application errors or system failures. An effective log analysis tool allows the IT team to access large amounts of data to proactively identify performance issues and prevent interruptions.
Log analysis is typically done within a log management system, a software solution that gathers, sorts and stores log data and event logs from a variety of sources.
Log management platforms allow the IT team and security professionals to establish a single point from which to access all relevant endpoint, network and application data. Log analysis typically includes:
Installing a log collector to gather data from a variety of sources, including the OS, applications, servers, hosts and each endpoint, across the network infrastructure.
Aggregating all log data in a single location as well as a standardized format regardless of the log source. This helps simplify the analysis process and increase the speed at which data can be applied throughout the business.
Leveraging a combination of AI/ML-enabled log analytics and human resources to review and analyze known errors, suspicious activity or other anomalies within the system. Given the vast amount of data available within the log, it is important to automate as much of the log analysis process as possible. It is also recommended to create a graphical representation of data, through knowledge graphing or other techniques, to help the IT team visualize each log entry, timing and interrelations.
The log management system should leverage advanced log analytics to continuously monitor the log for any log event that requires attention or human intervention. The system can be programmed to automatically issue alerts when certain events take place or certain conditions are or are not met.
Finally, the LMS should provide a streamlined report of all events as well as an intuitive interface that the log analyzer can leverage to get additional information from the log.
The Open Web Application Security Project (OWASP) is a nonprofit foundation that aims to improve software security by publishing industry standards, articles, tools, and documents. An example of the kind of tools it provides is the OWASP Risk Assessment Framework, which combines static application security testing and risk assessment tools.
Every three to four years, OWASP updates its list of top ten application security risks in light of prevailing application security dynamics and the overall threat landscape. The top ten are ranked in order of risk level.
Aspirapps's EQShield provides multi-layered protection to make sure websites and applications are available, easily accessible and safe. The EQShield application security solution includes:
Maintain uptime in all situations. Prevent any type of DDoS attack, of any size, from preventing access to your website and network infrastructure.
Enhance website performance and reduce bandwidth costs with a CDN designed for developers. Cache static resources at the edge while accelerating APIs and dynamic websites.
Analyzes your bot traffic to pinpoint anomalies, identifies bad bot behavior and validates it via challenge mechanisms that do not impact user traffic.
Protects APIs by ensuring only desired traffic can access your API endpoint, as well as detecting and blocking exploits of vulnerabilities.
Uses an intent-based detection process to identify and defends against attempts to take over users’ accounts for malicious purposes.
Keep your applications safe from within against known and zero‑day attacks. Fast and accurate protection with no signature or learning mode.
Mitigate and respond to real security threats efficiently and accurately with actionable intelligence across all your layers of defense.